Welcome. First off, I'm not sure how to write this properly nor do I know what exactly is this writing be named, let's just call this posting "shitposting" but this is going to be long one and maybe a useful one. I apologize if you find my language or wording is kinda weird or improper, I'm not native English speaker and never want to be one, but I'm good at swearing, trust me.
In this post, I will tell you how I gained access to vapehost.cc, lets just call this "target", and did what I want to its server, actually the last time I did this was a long time ago maybe around 6-8 years ago, I dont remember, and I never want to do this stupid thing again, but long story short the "boy" inside me is VERY ANGRY with the arrogance of the server's admin. So here it all begins.
First, I leaked the public_html.zip which contains website files of the target in VIP section, I NEVER even knew if the server's admin is here. Sometime after, the target's admin replied that it only contains useless thing about his website, meaning only JS, CSS, HTML and other USELESS thing you can think of, but it WASN'T useless, because I found another important/sensitive files, more on this later. I then appologized about the leak. After we talk to each other on the thread, it got deleted, I assume this is per his request. I then politely told him on his sales thread to secure his server, because remember, I have his very sensitive files which is, if I remember correctly, was called clients.zip, I say this is very sensitive because it MAY contain pretty much everything about the server, more on this later. He replied arrogantly that his server is SAFE and called me "KID". I assume this is an insult because, first, if the "kid" word is referred to a young person, then I'm not, he has no idea how long I've been living in this earth, and second, if the "kid" word is referred to as a "script kiddie", well I thought: "okay but I've already gained PHP shell access to your site, let's see who is the kid". The question is, how do I uploaded my PHP shell at the first place? Well, there are many ways to upload PHP shell, the one I used was a wordpress based exploit on one of his client's site, I didn't remember which one. But how did I found those sensitive files? The server was minimally hardened, the PHP functions to execute commands was disabled server-wide, enabling it by manually overriding the php configuration also gave me no luck, I can't feed my shell with any fucking linux shell commands, thats irony right? But I'm still left with 2 options, the first option is to use CGI shell and the second option is to use specially crafted PHP shell to read all of the server's username. I went with the second options, because PHP is my daily programming language, so to speak. But what info can be useful from a server's username list? Usually when I got PHP shell access, what I do next is looking for the main hosting username because if I can find it, it means I can possibly take over the whole server, this means, more advantages.
https://pastebin.com/FPnWe8Xf
So after I successfully read it, what to do next? I was unable to read the home directory of the target's username even though I knew the web's path which was "/home/vapehost/public_html", but this is where my "private" exploit I used comes into play. If you don't know what this is about, well, I suggest you to learn about privilege escalation on linux kernels, there are many public working PoC out there but the success rate is kinda low. So long story short, I was only able to see what was inside the username "vapehost", I was unable to get "root" access, I can't do anything here other than just to read it's directory structure. I was unable to read files, maybe due to permission settings or a bug in my exploit, I admitted I haven't researched more about this yet. And this is how I actually found those USELESS and VERY SENSITIVE files I said at the begining of this post. Since I know the directory structure, I can just go to "https://vapehost.cc/public_html.zip" and "https://vapehost.cc/clients.zip" on my browser to download those files, and I leaked public_html.zip shortly after. He claimed I was using lame URL dictionary attack enumeation or brute force or whatever the fuck he was referring to, thus maybe why he called me "kid" and said it was only useless shit.
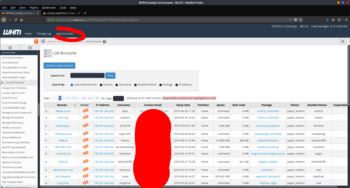
Next, what to do with that 'possibly' sensitive file "clients.zip"? I haven't even know whats inside, but I can guess, so I gave it a look and my guess was right, it contained WHMCS client & server management application files, including its config (configuration.php), this is the SENSITIVE file I am referring to. With this file, I can see database credentials and encryption key used to store the data about his clients & servers.
<?php $license = 'WHMCS-fa22c0ca70371a32aa4c'; $db_host = 'localhost'; $db_username = 'vapehost_whmcs'; $db_password = 'ZaGyHx7QSzBFvFKg'; $db_name = 'vapehost_whmcs'; $cc_encryption_hash = 'FWS8iQJwpEG9levun3tYkjPQNZx3aulFh3EpKdMZIiZTnkeBexpoH54kUrdVLorT'; $templates_compiledir = '/data/vapehost/templates_c/'; $mysql_charset = 'utf8'; $attachments_dir = '/data/vapehost/attachments/'; $downloads_dir = '/data/vapehost/downloads/';
I was sure it will work, but my shell was kinda outdated that I couldn't interact with the SQL server, this is due to that I still use the same constructor name with the class name on Database interaction class within my shell, and this is outdated, not just deprecated, don't worry, this is only a note for myself. So fuck this I have no time to rewrite the code, lets just grab a simple database management script. So I fetched a decent one from adminer.org and yeah I was successfully logged in and dumped the full database. I can already see the root password including every client's password, but fuck they were all encrypted and I had no idea what kind of encryption was it. I remember when I was playing with WHMCS a long time ago, because I did learned a bit about shared hosting business, I tried to decompile the code because it was encrypted using ioncube, from the results, I know what encryption was used by WHMCS to encrypt the database contents, there's even a decryption function available. So I grabbed the decryption function and wrote a simple PHP script to decrypt all those damn encrypted passwords I wanted to see! And voila, I got everything about the server including its root password.
Click to enlarge:
But what to do next? Well, remember, the boy inside me is VERY ANGRY, so fuck lets just dump all the databases in the server and drop it after finished, and upload some lame defacement page to it.
Click to enlarge:

Moral of the story: never judge a book by it's cover and be nice to everyone, you have no idea what they are capable of. And by the way, I'm offering whitebox penetration testing service to hosting companies, don't hesitate to contact me if you're interested in my service ![]()
 Sign In
Sign In Create Account
Create Account